How Apple's AI roadmap validates the Web3 thesis
data security is broken; blockchain-orchestration can fix it
Data security is broken
Centralized data networks, ones that are owned and/or managed by a single entity, have been structurally broken for years. The reason? Single points of failure. If one entity (or even a few) has access to a database, then there is only one “point” to compromise in order to gain full access. This is a serious problem for networks holding sensitive data like customer information, government files, and financial records, and those with control of infrastructure like power grids.
Billions of digital records were stolen in 2024 alone, causing an estimated $10 trillion in damages! Notable breaches include nearly all of AT&T’s customer information and call logs, half of America’s personal health information, 700 million end-user records from companies using Snowflake, 10 billion unique passwords stored on RockYou24, and Social Security records for 300 million Americans.
This is not just a private sector issue - governments and crucial national infrastructure also rely on centralized networks. Notable recent breaches include China’s hack of US Treasury workstations, records on 22 million Americans stolen from the US Office of Personnel Management, sensitive government communications from multiple US federal agencies, personal biometric data on 1.1 billion Indian citizens, and the ongoing Chinese infiltration of several US internet service providers.
Although hundreds of billions of dollars are spent each year on cyber security, data breaches are getting larger and happening more frequently. It’s become clear that incremental products cannot fix these network vulnerabilities — the infrastructure must be completely rearchitected.
AI magnifies the issue
Recent advancements in generative AI have made it easier to automate everyday tasks and enhance work productivity. But the most useful & valuable AI applications require context, i.e. access to sensitive user health, financial, and personal information. Because these AI models also require massive computing power, they largely can’t run on consumer devices (computer, mobile), and instead must access public cloud networks, like AWS, to process complex inference requests.
Given the serious limitations inherent in centralized networks illustrated earlier, the inability to securely connect sensitive user data with cloud AI has become a significant hurdle for adoption. Fortunately, there is a Web3 solution: blockchain-orchestrated confidential clouds (BOCCs). But don’t take my word for it, just ask Apple.
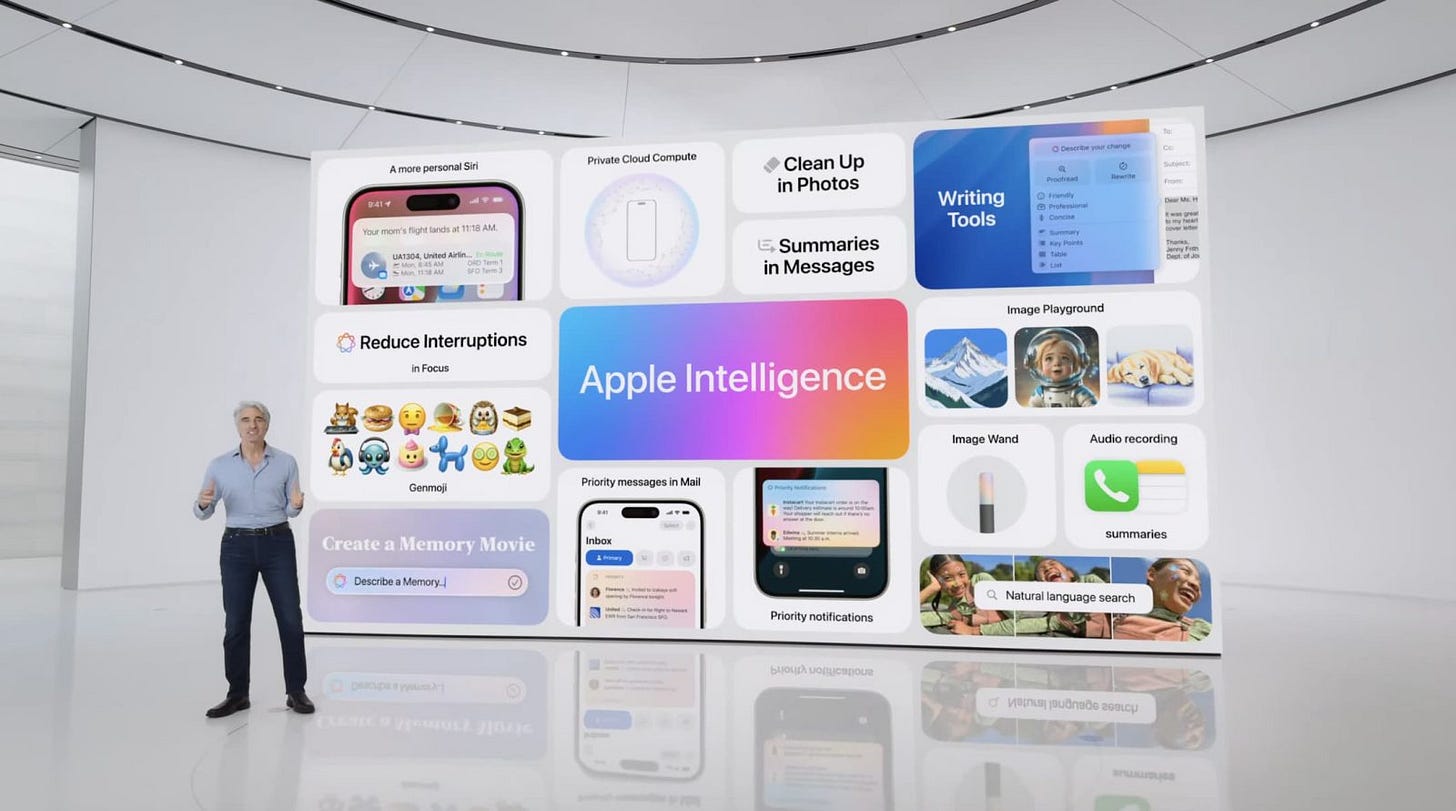
Apple Intelligence unveiled
In June of this year, at the Worldwide Developers Conference (WWDC), Apple unveiled its vision for Apple Intelligence, an AI system designed to enhance user experiences across iOS, iPadOS, and macOS. Given the limitations of consumer devices, these new features must leverage cloud resources; however, Apple points out these cloud networks are fundamentally broken.
Apple needed an alternative cloud solution, but since none exist in Web2, the company ultimately decided to just build one themselves: Private Cloud Compute (PCC).
Reading through PCC’s technical blueprints, Apple’s next-gen, AI-centric cloud looks identical to BOCC architecture (albeit with inferior security). This technical revelation not only validates the thesis for Web3 infrastructure but demonstrates the structural superiority of decentralization in securing these networks.
Let’s dive in.
Technical shortcomings of today’s cloud
Apple describes three main reasons why today’s cloud infrastructure is not suitable for AI integration.
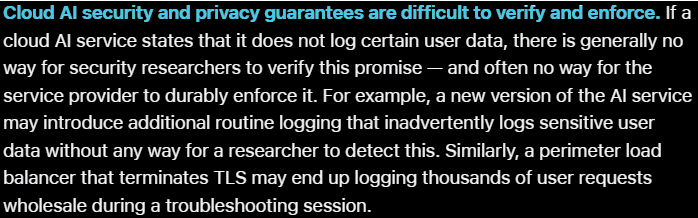
No way to verify privacy and security:
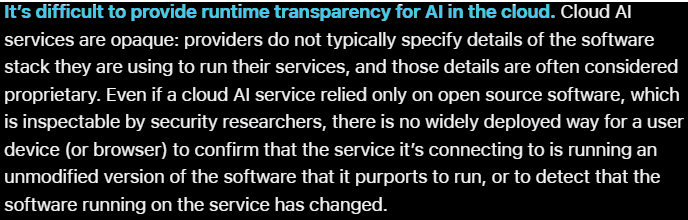
Users can’t confirm they’re connecting to the correct AI:
Single point of failure:
Blockchain-Orchestrated Confidential Cloud (BOCC)
Before we explore PCC’s architecture, it’s important to first understand how BOCCs work. The best example of this architecture is Super Protocol: an offchain enterprise-grade cloud platform, managed completely by onchain smart contracts and built on trustless execution environments (TEEs; secure hardware enclaves that keep code & data verifiably confidential and secure).
The implications of this technology address all of Apple’s concerns noted earlier.
Privacy and security verification: With public smart contracts orchestrating the network, users can verify whether user data was transported and used as promised.
Workload & program transparency: The network also verifies the work done within the confidential TEEs, cryptographically proving the correct hardware, data, & software were used, and the output wasn’t tampered with. This information is also submitted onchain for all to audit.
Single point of failure: Network resources (data, software, hardware) are only accessible by the owner’s private key. Therefore, even if one user is compromised, only that user’s resources are at risk.
Apple’s PCC Architecture
Now let’s take a look at Apple’s solution, which is so similar to BOCC its shocking.
Privacy and security verification: It similarly governs network resources completely through software programs (like smart contracts), which are publicly available for audit on Apple’s transparency log (like a blockchain).
Workload & program transparency: PCC also leverages TEEs to keep user data confidential & verify the correct hardware, software, and data were used, and that the output was not tampered with.
Single point of failure: User data & network resources can only be accessed through individual private keys.
But wait - doesn’t this just mean big tech can just copy Web3 architecture, rendering blockchain-orchestrated networks obsolete?
No, and this is the most important part to remember:
The key difference!
Apple describes its “transparency log” (its version of a public ledger) as “append-only and cryptographically tamper-proof”. Sounds like blockchain right? Wrong - this log is still owned and operated by Apple. There is no way to verify that this information hasn’t been tampered with, including the network management code and private/public keys, creating a crucial single point of failure for the entire PCC platform.
All it takes is one piece of the tech stack to be centralized for the entire stack to be centralized. Apple can only say “trust me bro”.
Web3 thesis validation
I was excited the first time I read Apple’s announcement, thinking the “transparency log” was a euphemism for blockchain. The reality is actually more exciting:
Apple set out to create the optimal cloud environment for AI applications and created a near-replica of the BOCC design, validating the key Web3 thesis of verifiably private & secure cloud computing.
Apple (and any other entity that creates similar architecture) will always have inferior security guarantees because they own and operate the transparency logs as well as the physical compute infrastructure (single point of failure).
BOCC > PCC
While cloud AI represents an enormous opportunity for Web3 to disrupt, BOCCs can be applied to any type of centralized data network (power grid, digital voting infrastructure, military IT, etc.), to provide superior & verifiable privacy and security, without sacrificing performance or latency.
Our digital infrastructure has never been more vulnerable, but blockchain-orchestration can (and must) fix it.
About M31 Capital
M31 Capital is a global investment firm dedicated to crypto assets and blockchain technologies that support individual sovereignty.
Website: https://www.m31.capital/
Twitter: https://twitter.com/M31Capital