Trustless Execution Environments
why TEEs are optimal networking infrastructure for Web3 and DeAI
Rethinking the use of Trusted Execution Environments (TEEs), transforming it from a “trusted" environment into a "trusted due to verification" or TRUSTLESS Execution Environment, is essential. This is achieved by integrating smart contracts, cryptographic primitives, and widely used network technologies, leveraging TEE's embedded security to control operations within the TEE and ensure compliance through blockchain consensus mechanisms. By combining blockchain technology and TEEs, Web3 and AI can ensure trustless computing environments where computations are secure, verifiable, and transparent.
Nukri Basharuli (Super Protocol) | David Attermann (M31 Capital) | ₿RRR Rezo (BR Capital) | Jeremy (Aizel Network)
Table of Contents:
Intro: TEE as Enabler for Trustless Computing
In the crypto world, trust is fundamental.
The concept of a "Web of Trust", which we widely use in crypto, was first introduced by Phil Zimmermann, the creator of PGP (Pretty Good Privacy) encryption software, in 1992.
But we don't simply trust. "Don’t trust, verify" is a fundamental principle in the field of cryptography and cybersecurity. It emphasizes the importance of not just accepting information at face value but also validating it through verification processes.
Blockchain's core strength lies in verifiable code – scripts, consensus algorithms, and smart contracts – which establish trust by ensuring system reliability, transparency, and verifiability. However, trust extends beyond code. In a decentralized system, the transparency of physical infrastructure, particularly the servers and equipment performing computations, is equally crucial. This is where CPUs and GPUs come in. While these computational resources may seem inherently trustworthy, blockchain principles demand verification. After all, the core tenet of blockchain is "don't trust, verify."
Decentralized computation relies on consensus and verification to ensure the accuracy of operations. For simple computations like transactions or smart contracts, multiple nodes can perform and compare calculations, guaranteeing reliable outcomes. Additionally, crypto-economics leverages game theory and penalties (like slashing) to deter malicious actors from submitting incorrect data or transactions. This combination of consensus, verification, and economic incentives maintains order and security within the system.
However, verifying complex computations like those in AI becomes expensive and impractical with traditional methods used for simple transactions. This limitation hinders scalability. This article explores Trusted Execution Environments (TEEs) – a technology within CPUs and GPUs – and how they address this challenge. We'll delve into how the "Trusted" aspect of TEEs can be verified within a trustless Web3 system. By adhering to core blockchain principles like open-source code, consensus mechanisms, smart contracts, cryptography, and verifiable computation machine attestations, TEE-based Web3 systems can achieve trustlessness while maintaining scalability, openness, and transparency.
TEE Use Cases Today
In short, TEEs represent secure and confidential computational environments within CPUs or GPUs that isolate code execution and data processing from the rest of the device. This technology protects code execution from external influences, even if the operating system or hardware environment is compromised.
Key Features:
High Security: TEE encryption ensures data is protected at all times, both at rest and in use.
Confidentiality: Sensitive data remains confidential, even if the main system is compromised.
Integrity: The integrity of the data and code is maintained, preventing unauthorized modifications.
Isolation: The TEE provides an isolated environment, ensuring secure execution of sensitive operations.
Verification: TEE provides attestation of computing results to ensure they haven’t been tampered with by untrusted parties.
All of us, including proponents and ardent followers of decentralization, “trust” TEE daily in many popular devices and services that support everyday security technologies. For instance, TEE is actively used in:
iPhones, iPads & Android devices: generating, and securely storing and processing encryption keys for data protection, biometrics, and many other sensitive data / processes.
Signal Messenger uses TEE for private contact discovery, biometrics, storing user data, protecting sensitive operations.
And, hold on a second - even the most popular cold crypto wallet - Ledger - uses TEE to generate, store keys and sign transactions.
Other prominent uses of TEE include HTTPS connections, storing private keys of root certificate authorities, Cloudflare and systems that ensure the security of payment cards.
The above underscores the importance and seriousness of TEE technology. But obviously, its applications are far broader and more extensive. TEEs are now embedded in all CPUs & GPUs from giants like Intel, Nvidia, AMD, ARM, Qualcomm, Samsung, IBM, and others. Even Cerebras, who's building AI-specific mega-chips, have TEE.
The near-universal adoption of TEE by chipmakers speaks volumes about its potential. Trusted Execution Environments (TEEs) are already embedded in the chips we use daily, securing everything from biometric authentication to complex AI models. If TEEs are trusted to safeguard sensitive data in these critical tasks, can we use them in crypto?
The answer lies in verification. Blockchain systems require verifiable computation, which goes beyond just secure execution. Here's where TEEs excel: they come equipped with cryptographic attestation, which guarantees the code running in the secure enclave is genuine and hasn't been tampered with.
How TEEs Achieve Verifiability
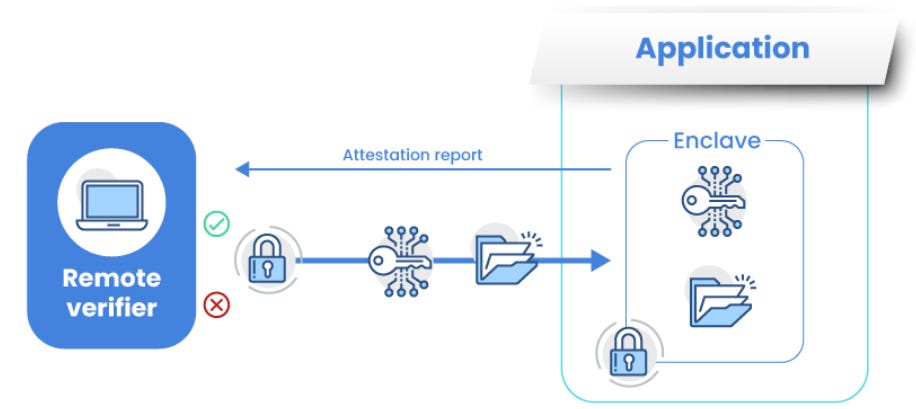
TEE encryption works by generating and securely storing cryptographic keys within an isolated execution environment. It encrypts and decrypts data using these keys, ensuring data remains confidential and protected from unauthorized access. Secure channels are used for communication, and the integrity of the TEE is maintained through a hardware root of trust and attestation processes.
The following steps illustrate how TEEs achieve security and verifiability through encryption and attestation:
Initialization
Secure Boot: The process starts with a secure boot, ensuring the firmware and software loaded are trusted. This establishes a root of trust for the TEE.
Key Generation
Private Key Generation: A unique private key is generated within the TEE using a cryptographically secure random number generator. This key is highly complex and has high entropy, making it resistant to hacking.
Key Storage: The private key is stored in the TEE's secure storage, which is typically implemented using hardware-based mechanisms to prevent unauthorized access.
Encryption and Decryption
Data Encryption: When data needs to be protected, it is encrypted using the private key or a session key derived from it. The encryption process converts the plaintext data into ciphertext, which is unreadable without the corresponding decryption key.
Data Decryption: To access the protected data, the TEE decrypts the ciphertext back into plaintext using the private key or session key. This decryption process is done securely within the TEE to ensure the data remains confidential.
Secure Execution
Isolation: The TEE provides an isolated execution environment where sensitive code and data are processed. This isolation ensures that even if the main operating system is compromised, the data within the TEE remains protected.
Runtime Protection: During execution, the TEE ensures that data and code are protected from unauthorized access and tampering. This includes protecting against side-channel attacks and other vulnerabilities.
Communication
Secure Channels: When data needs to be communicated outside the TEE, secure channels are used. These channels encrypt the data during transmission, ensuring it remains confidential and intact.
Public Key Exchange: The TEE can generate a public key corresponding to its private key. This public key can be shared and used to establish secure communication channels with external entities.
Integrity and Verification
Hardware Root of Trust: The TEE leverages a hardware root of trust to verify the integrity of the system. This includes checking that the firmware, software, and keys have not been tampered with.
Attestation: The TEE can provide attestation through a cryptographic process, where it proves to external parties that it is running trusted code and that the keys have not been compromised.
Throughout this process, TEEs achieve a verification of computing results which makes them trusted.
In this article we want to go further and show that by integrating TEEs with smart contracts, cryptographic primitives, and established network technologies, Web3 community can move beyond "trust” and achieve decentralized and verifiable Trustless Execution Environments.
Misconceptions of TEE Security
Bagel Network recently published an article exploring the pros and cons of using TEE technology for AI applications. The report did a great job of explaining the technology, and the benefits it brings to Web3 & AI, but we believe it misrepresents the security of modern TEE systems. Specifically, the authors call out Replay Attacks, Host-Based Attacks, Access Pattern Exploitation, and Side-Channel Attacks:
Replay Attacks: Replay attacks involve intercepting and retransmitting valid data to create unauthorized effects. For instance, an attacker might replace a newer message with an older one from the same sender, effectively resetting the state of a computation.
Host-Based Attacks: Host-based attacks exploit vulnerabilities arising from the interactions between the host operating system (OS), user-space processes, and the TEEs running on the same system.
Access Pattern Exploitation: Previous research has demonstrated methods to exploit access patterns to TEEs to classify encrypted inputs with high accuracy. This type of attack can reveal sensitive information about the data being processed within the TEE.
Side-Channel Attacks: Side-channel attacks exploit indirect information leakage from the TEE, such as timing, power consumption, electromagnetic emissions, or memory access patterns.
Below we explain the mitigants for each attack vector mentioned:
Replay Attack: This is still related to software operating within the enclave. If the software takes into account the possibility of state substitution, the attack will be impossible. For example, in SGX, there is an option to get trusted time (get_trusted_time). This is usually used to prevent state resets or repeated calls with the same data.
Host-Based Attack: This scenario is impossible if the software within the enclave accounts for the fact that the OS kernel is untrusted. In SGX, there is a clear separation between trusted and untrusted calls. The articles referenced do not describe how a compromised OS can be used for an attack in the absence of vulnerabilities in the enclave software.
Access Pattern Exploitation: This type of attack can somewhat deanonymize the application by revealing the nature of the data it uses, but not the data itself. In more modern systems like Super Protocol, the TEE owner does not know which specific application is running on their infrastructure, and gathering information about the nature of data used by random applications is unlikely to be of any use to an attacker.
Side-Channel Attack: This is the most realistic of all attack vectors, but again, side-channel attacks are labor-intensive and therefore costly, with no guaranteed results. Ethereum or Bitcoin can also be compromised by the notorious 51% attack (or more commonly around 33%), but this would require substantial financial investment. In most IS, security is actually based on the balance of the cost of the attack versus the economic benefit. In the case of TEE, the balance is very good.
Despite numerous studies and discovered vulnerabilities that could potentially lead to data leaks, there are currently no known practical cases of their exploitation by attackers. Most vulnerabilities are either completely patched or their application is significantly limited. These types of attacks typically involve extensive, prolonged examination of the application, possibly with multiple restarts, before finding a way to extract a secret.
TEE x Blockchain for Sovereign AI
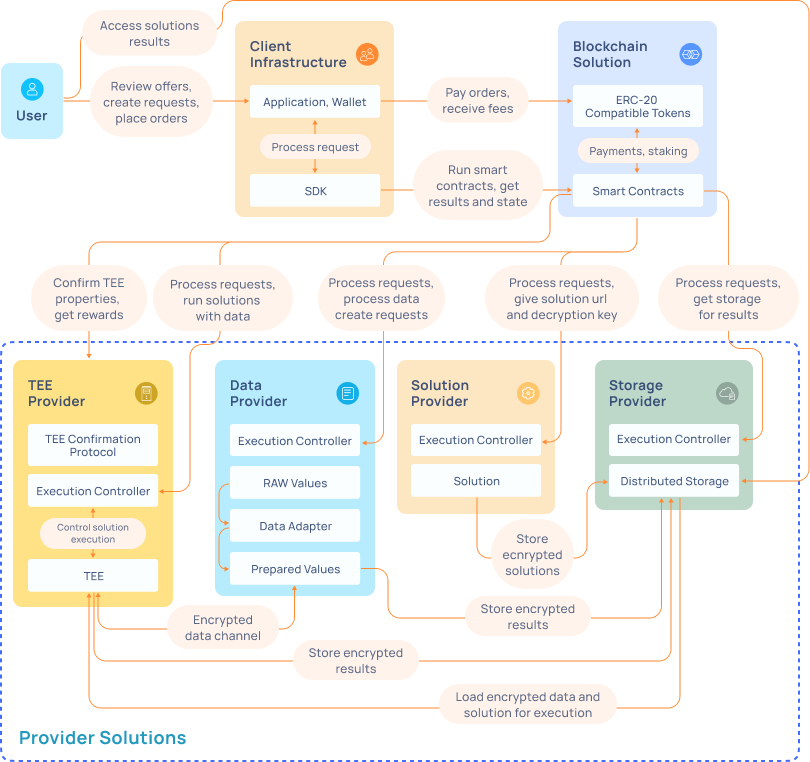
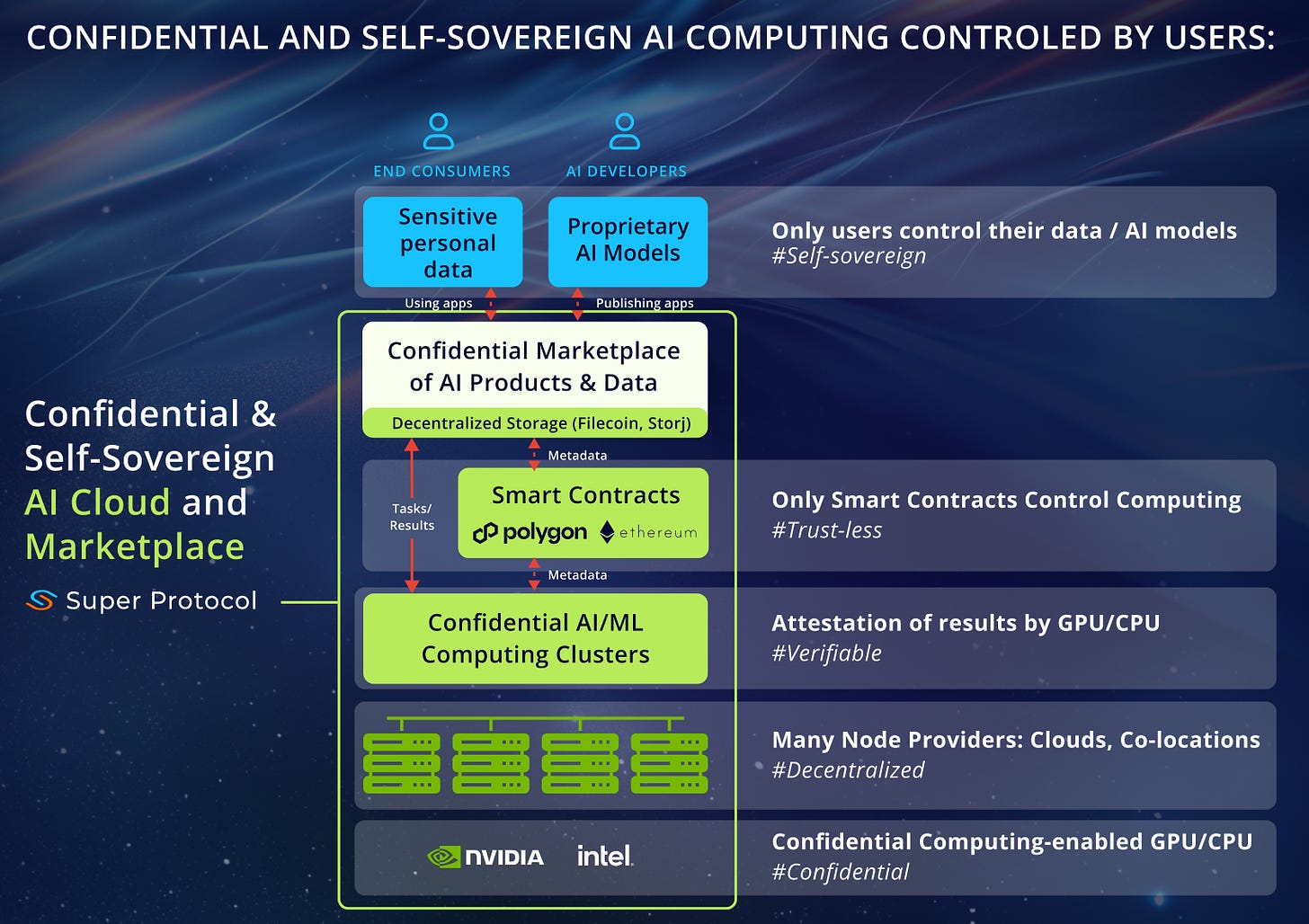
Super Protocol is a great example of how TEEs and blockchain technology can work harmoniously together, in this case, to power a trustless (verifiable), secure, and confidential full-stack cloud computing platform – suitable for high-performance computing like AI.
By combining smart contract governance with clusterized TEE computing capacity from a variety of providers, Super Protocol eliminates human administration from the cloud governance, enabling trustless and Web3-compliant AI computing.
Here’s a quick overview on how it works:
Task Submission
Users upload their computing tasks to the blockchain.
Each task is recorded with a unique identifier.
Task Assignment
Users assign tasks to available TEE resources.
Task assignments are transparent and can be tracked on the ledger.
Secure Execution
TEEs execute tasks in a secure and isolated environment.
Data is encrypted and protected from unauthorized access during processing.
Proof Generation
Upon task completion, TEEs generate cryptographic proofs of execution.
These proofs are submitted to the blockchain for verification.
Consensus Verification
The blockchain network verifies the cryptographic proofs.
Consensus mechanisms achieve agreement on the state of the network.
Result Delivery
Verified results are delivered back to the user.
Users can access the results and the corresponding proof on the blockchain.
Reward Distribution
TEE providers receive tokens as rewards for their services.
Smart contracts automate the payment process based on task completion and verification.
By leveraging blockchain technology and TEEs, Super Protocol creates a Тrustless computing environment where computations are secure, verifiable, and transparent. This process ensures that users can “trust” the results without needing to rely on a central authority.
Moreover, Trustless computing enables Trustless collaboration between AI companies and data owners via a secure and verifiable AI marketplace. This allows companies to leverage valuable data and models for AI development without compromising confidentiality or security.
Essentially, Super Protocol's technology could be the foundation for a "Web3 Hugging Face" - a decentralized platform for sharing and utilizing AI models, with the added benefit of zero-disclosure monetization through a native token. The basic flow looks like this:
Data and Model Uploading: Data owners and model developers could upload their assets to the decentralized storage, specifying usage rights through smart contracts. These smart contracts would also define the associated fees in the platform's native token, enabling zero-disclosure monetization.
Task Submission: AI developers could submit training or inference tasks referencing these models on the blockchain, paying the required fees in the native token.
Secure Execution: Tasks would be assigned to TEE providers, ensuring data remains confidential during computation.
Verifiable Results: TEEs would generate proofs of execution, verified by the blockchain for accuracy.
Reward System: Smart contracts could manage payments to data owners and model developers based on usage, automatically distributing the platform's native token according to the pre-defined fees.
This “Web3 Hugging Face” would foster open collaboration and innovation in AI by enabling secure, verifiable, and permissioned access to valuable resources, while simultaneously allowing data owners and model developers to monetize their assets without revealing sensitive details through the use of a native token.
Why DePIN is Incomplete Without TEE
The rise of Decentralized AI (DeAI) fuels the demand for trustless GPU marketplaces in Web3. With GPU DePIN networks rapidly gaining traction in the Web3 landscape, the issue of verifying the resources they offer becomes paramount. At the same time, DePIN networks, while promoting decentralization, face limitations in guaranteeing the verifiability and security of off-chain resources.
However, as the recent io.net fiasco illustrated, verifying the legitimacy and availability of DePIN resources within these marketplaces is crucial.
Decentralization is not enough. Unprotected virtual machines are vulnerable to fake servers, jeopardizing sensitive data. On the other hand, TEEs provide a secure alternative. Manufactured with unextractable private keys, TEEs are inherently tamper-proof. Additionally, attestation verifies the environment's authenticity and soundness. This combination of hardware security and verifiable integrity makes TEEs ideal for securing sensitive tasks in decentralized systems.
TEEs are impossible to fake, because they are manufactured with unextractable embedded private keys. Unlike unprotected virtual machines, with which hundreds of thousands of fake servers can be inserted into the network undetected, TEE technology supports an attestation process that enables verification of the authenticity and soundness of the execution environment.
We believe that DePIN will inevitably evolve to TEE-based architectures, powered by platforms like Super Protocol:
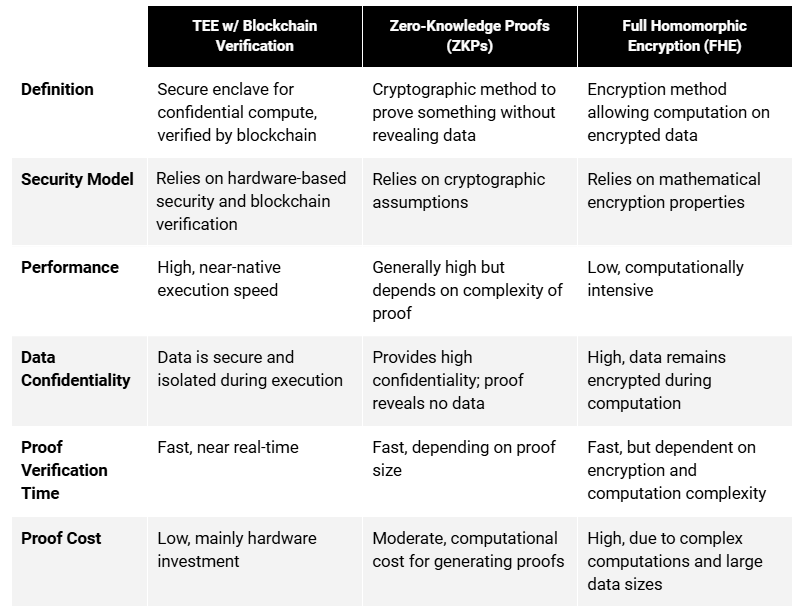
TEE vs Verifiable Computing Alternatives
When integrating TEE into blockchain systems, scalability and performance issues must be considered. With regard to high security demands, which can in other cases slow down operations (such as with Fully Homomorphic Encryption or Zero Knowledge Proofs), properly designed systems using TEE can scale efficiently without creating excessive burdens. This sets them apart from other alternatives for systems requiring privacy and confidentiality.
To sum it up, TEEs offer several key advantages for Web3 high-performance computing AI systems, including:
No performance degradation: Ensuring high security without sacrificing speed.
Utilization of popular open-source products for scalability: Leveraging well-supported tools to enhance system capabilities.
Network tools for building computational clusters and pools: Facilitating the creation of robust, scalable computing environments.
Management of containerized workloads and services: Efficiently handling various tasks within secure containers.
Secure verification of input, output, and running processes: Ensuring the integrity and confidentiality of all computational activities.
TEEs for AI Coprocessing
We’ve so far discussed the advantages of using blockchain orchestrated TEEs for general Web3 computing and DeAI applications. But what if smart contracts could directly leverage the power of AI to help complete highly complex, tedious, and novel software operations? This is where AI coprocessors come in, an unprecedented and paradigm-changing breakthrough for the entire Web3 space.
How do we ensure that AI, powered by centralized computing entities and generated entirely in a black box, can form unity and consistency with strictly decentralized systems like blockchains? In other words, how can we trust off-chain AI in an on-chain environment? The answer is simple: on-chain verification. However, the implementation is extremely complicated and has become the most significant technological gap preventing Web3 from integrating with AI.
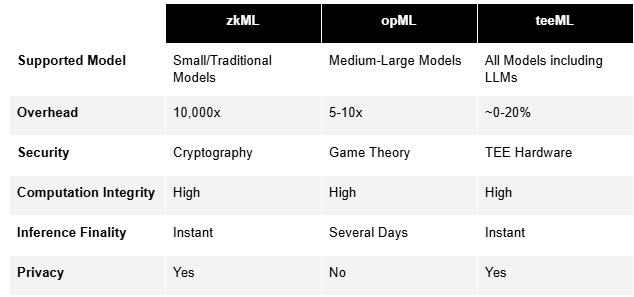
Vitalik Buterin recently wrote a blog about Crypto and AI, summarizing the path to trustless AI technologies, which fall into three categories: zkML, opML, and teeML:
zkML (Zero-Knowledge Machine Learning): Utilizes a zero-knowledge proof system optimized for machine learning tasks to generate proofs for machine learning model inferences to guarantee the integrity and verifiability of AI. Its execution strictly follows cryptography and has the most orthodox pedigree in ensuring the integrity and verifiability of AI, as well as the privacy of users who use the model. It is very suitable as a proof of concept, but its advantages pretty much end here. Even the most advanced zkML proof systems are still in the theoretical research stage for proving a regular-size machine learning model. According to public research and results, the overhead required to prove an inference for a large Transformer 2-level model is around 3-14 days, which is still really very far from production-ready. While ZK technology achieves step-function improvement nearly every 4-5 years, due to the characteristics of ZK itself, the overhead of zkML increases almost exponentially as the model size increases, which makes the final implementation of verifiable execution of large models based on zkML a major challenge.
opML (Optimistic Machine Learning): A cross-validation method and incentivization mechanism similar to OP rollups that error-check and challenge the executions of the machine learning models, thereby achieving the verifiability of AI. opML achieves a considerable improvement in computation overhead compared to ZK, however, this non-computerized method, heavily relying on human incentivization, is generally less reliable than zkML, which strictly follows cryptography. Also, similar to OP rollups, such a method takes several days to achieve the finality of model inference. Furthermore, opML doesn't protect user privacy, with the user's input, execution process, and output all being fully open and transparent.
teeML (Trusted Execution Environment Machine Learning): Under teeML, machine learning model inference, including large language models, can be executed in the hardware-based TEE environment and proved along with the corresponding attestation reports. At the same time, its overhead is almost similar to the cost of using untrusted regular machine learning models in Web2. Not only can model inference be finalized immediately, but users' privacy using the model can also be wholly guaranteed. Since the cost of tampering hardware-based TEE technology is extremely high, the technology enjoys the unique combination of security, speed, cost, and privacy for AI verifiability.
Given the serious limitations of zkML and opML, teeML is the most practical technology for achieving AI verifiability for the next 3-5 years.
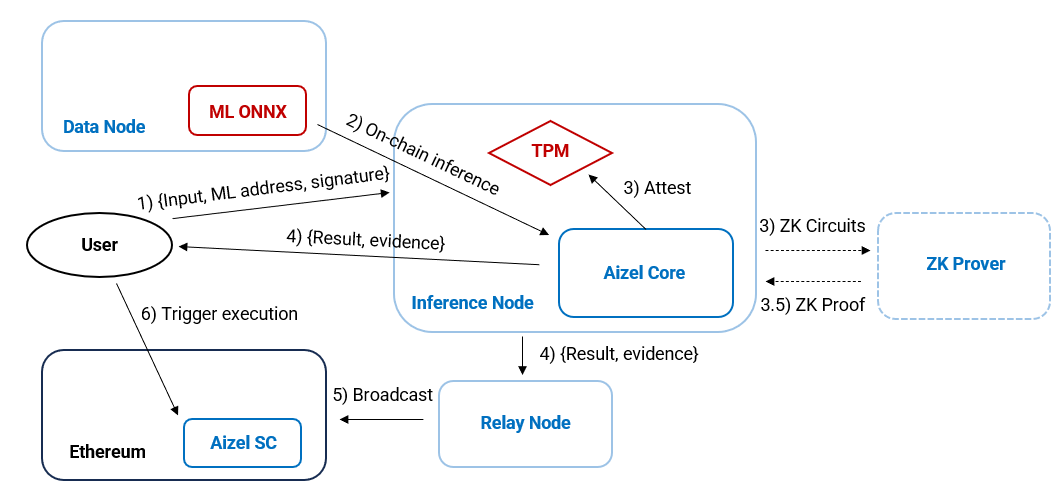
Aizel Network is a pioneer in teeML, leveraging TEEs to ensure the end-to-end inference and execution process of machine learning models, including LLMs, occurs in a trustworthy environment. Based on the attestation reports generated by TEEs, AI inferences and executions can be verified by all relevant parties. With its MPC framework on top of TEEs, Aizel can achieve the same level of security and decentralization as zkML by cutting specific inferences into multiple subtasks and distributing them to subnodes. The attestation system developed by Aizel can already achieve trustless execution of Llama3-level models with an overhead of less than 30% of the cost of inference, but they believe they can reduce it to 5% as the network matures.
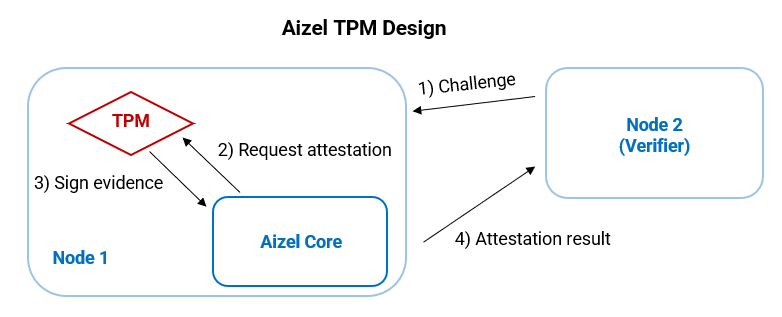
Aizel’s Inference Verification Technology:
Trusted Platform Module (TPM): A physical, secure cryptographic computer chip used by a remote party to attest to a system's integrity. Even if the physical chip ends up in the hands of adversaries, it’s nearly impossible to retrieve the private keys to hack the system successfully. Although the risk is low, Aizel also leverages decentralized MPC technology to secure the network further.
Multi-Party Computation (MPC): The decentralized MPC ensures the attestation process is highly secure, collectively done by a group of nodes chosen at random. This additional layer ensures the trustlessness of the remote attestation is nearly as high as that of the zkML approach.
Two other leaders in TEE coprocessing technology include Marlin Protocol and Phala Network:
Marlin Protocol is a well-established project in the field of verifiable off-chain computing, leveraging TEEs to process and integrate off-chain computing trustlessly with on-chain smart contracts. With the rapid development of on-chain AI, Marlin has become one of the first projects to explore the use of TEE for verifiable execution of any machine learning model. Marlin's Oyster solution can execute AI inference processes trustlessly, protecting user privacy with relatively low overhead.
Another successful project in the field of verifiable privacy computing is Phala Network, which has recently developed AI co-processors by upgrading its TEE's verifiable computing capabilities. It achieves AI verifiability through the tens of thousands of TEE chips in the Phala Network, giving smart contracts and blockchain users trustless AI-driven computing power.
Conclusion
In today's quickly evolving digital landscape, the integration of TEE with blockchain solves critical bottleneck problems, especially for handling and verifying heavy computations, addressing growing privacy threats, and advancing the era of Decentralized AI. TEEs enhance the security framework by isolating code execution and safeguarding sensitive data, thus reinforcing the integrity of decentralized platforms. Unlike more well-known verifiable computing technologies like ZKPs and FHE, which are optimistically 3-5 years away from practical implementations, TEE-based infrastructure is ready TODAY.
This compact exploration shows that TEEs can transform the notion of trust within DePIN ecosystems and other Web3 infrastructure from a traditional concept to one that is continuously verifiable. By leveraging smart contracts for governance within TEEs, we create a 'TRUSTLESS' environment where verification is inherent and automated. Such a setup not only protects against external and internal threats but also aligns with the decentralization ethos of blockchain, ensuring transparency sovereignty for users, data and computations.
As the demand for more secure, private, and efficient blockchain solutions grows, the role of TEEs is set to expand. Their ability to integrate seamlessly into existing blockchain architectures makes them indispensable in the development of future-proof blockchain infrastructures. This integration marks a significant step toward realizing blockchain's full potential, promising enhanced security and trust in an era dominated by complex digital interactions.
About the Authors
Nukri Basharuli | Founder & CEO Super Protocol
Nukri holds a PhD in Nuclear Physics and is a serial entrepreneur with over 13 years of experience in secure decentralized computing and IP processing technologies. Prior to creating Super Protocol, Nukri founded a blockchain orchestrated data collaboration platform, Aggregion, which won the 2020 Microsoft Partner of the Year Award.
David Attermann | Sr. Portfolio Manager M31 Capital
David has been investing in crypto since 2014 and currently leads liquid and illiquid Web3 investments at M31 Capital. He specializes in infrastructure and middleware technology and previously co-founded Omnichain Capital, a thesis-driven liquid token fund. David started his career in traditional finance, spending ten years advising and investing in networking technology companies.
₿RRR Rezo | Founder BR Capital
Rezo S. has been active in the crypto space since 2016. He founded BR Capital in 2018, focusing on Quant trading and VC investments in DeFi, DAOs, and data, and is an early investor and advisor in Super Protocol. His current projects explore the intersection of AI and blockchain, aiming to build open, decentralized, and inclusive AI economies.
Jeremy | Co-Founder Aizel Network
Jeremy is a serial entrepreneur across Web2 and Web3 and starting crypto career as the investment head of a top-tier CEX. With a dual background from CS and Business, Jeremy co-founded Aizel in 2023 along with a few other tech veterans in Web3, building the fastest and most scalable modular network dedicated to verifiable AI, and accelerating the massive adoption of on-chain AI.
About M31 Capital
M31 Capital is a global investment firm dedicated to crypto assets and blockchain technologies that support individual sovereignty.
Website: https://www.m31.capital/
Twitter: https://twitter.com/M31Capital